HG Vulnerability Management Services (VMS) allow enterprises to immediately and materially improve their security risk posture through fully managed, consistent scanning of assets with business context, risk prioritization, timely remediation and actionable metrics.
We pride ourselves on prioritizing the continuous improvement of your HG Managed Service, along with the measured advancement of your security program. In order to do so, it is critical that synergies exist between your Security Assessment & Testing programs, your overall Security Operation Centre (SOC) Services and your Managed Detection and Response Capabilities. These synergies help ensure the detection, assessment, investigation, and resolver group initiation of potential threats before they become security incidents.
Herjavec Group believes in balancing Vulnerability Management, Penetration Testing and Red Team Operations as critical components to your Security Program. Adopting a regular network scanning cadence and risk-based evaluation for recommended next remediation activities is the first step.
Our Approach to Vulnerability Management
Managed Vulnerability, Reduced Risk
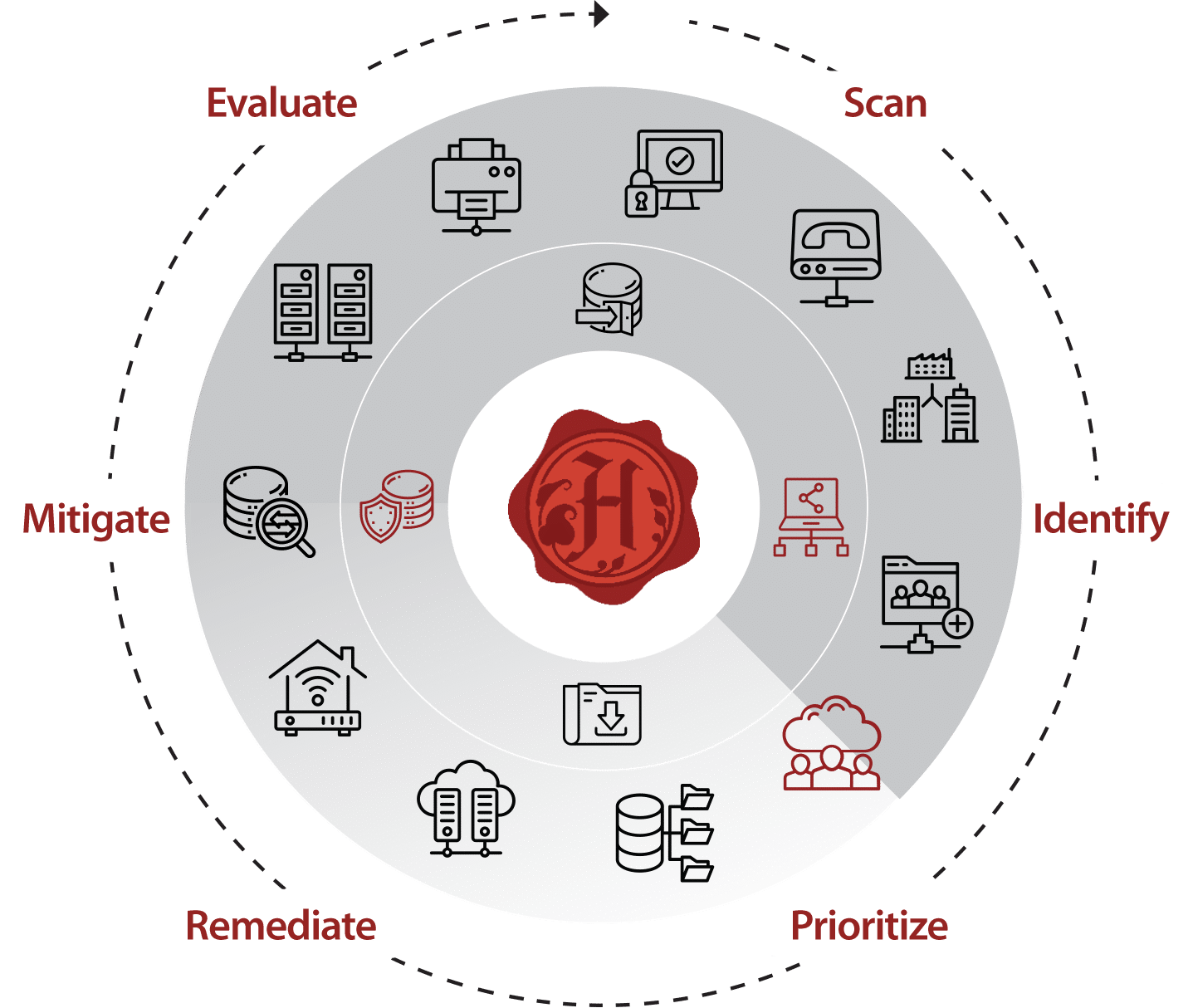
Our fully managed solution scans across your entire IT infrastructure, identifying vulnerabilities and prioritizing them with a risk-based evaluation. From there, we remediate vulnerabilities in sequence, track exceptions for future mitigation, or provide recommendations on compensating controls/segmentation. This process takes place on a regular cadence and is supported by a stakeholder report that summarizes the delta of prioritized vulnerabilities between scanning periods.
Managed vulnerability insights include:
- Number of Assets Scanned and Vulnerabilities Discovered
- Vulnerabilities with Malware Kit and Exploit Exposures
- Vulnerabilities Breakdown by Vulnerability Severity
- Total Vulnerability Breakdown by Asset Location
- Unique Vulnerability Breakdown by Asset Location
- Vulnerabilities Breakdown by Vulnerability Age
- Vulnerability Risk-based Scoring – Critical, Moderate, Severe
Why do you need Vulnerability Management?
Vulnerability Scanning is like a camera taking a snapshot in time. After the picture is taken, you can analyze it, understand the full scenario, and prioritize what needs to be addressed. However, new vulnerabilities are found every day making it essential to uncover and correct them. Taking snapshots on a regular basis will allow your enterprise to regularly assess and properly fortify your security posture accordingly. Vulnerability Management Services typically involve a network scanning program on a monthly or quarterly basis, supported by a stakeholder report summarizing the delta of prioritized vulnerabilities between scanning periods.
Vulnerability Management Addresses Common Enterprise Cybersecurity Challenges
Lack of comprehensive IT infrastructure and asset visibility
- Consistent scanning of 100% of your IT infrastructure, including external and internally facing devices
- Ongoing discovery of virtualized assets, closing any blind spots with an up-to-date asset inventory
- Confirmation of asset discovery and vulnerability changes between scanning periods
Complicated and tedious compliance processes and standards
- Adherence to compliance guidelines in terms of scanning cadence
Overwhelming number of known risks and vulnerabilities and lack of knowledge on how to prioritize which to address first
- Prioritization of remediation activities through severity risk-based scoring
Lack of in-house expertise and tools to properly assess cybersecurity posture scanning and testing results, and quickly remediate identified vulnerabilities
- Accurate understanding of real risk exposures with business context
- Timely response to and remediation of identified vulnerabilities
Difficulty understanding and communicating performance metrics and current security posture
- Stakeholder report including operational and executive metrics that measure the performance of your Vulnerability Management program
Difficulty achieving and maintaining regulatory compliance
- Compliance with data protection mandates in regulations such as the GDPR, HIPAA and PCI DSS, avoiding the impact of penalties and reputational damage
4 Components to a Strong Vulnerability Management Program
-
Asset & Vulnerability Discovery
-
Vulnerability & Risk Prioritization
-
Patch Management
-
Remediation & Exception Tracking
Your trusted partner
With 5 global Security Operations Centers, emerging technology partners and a dedicated team of security specialists, Herjavec Group is well-positioned to be your organization’s trusted advisor in cybersecurity.
100% Cybersecurity Focused
Laser-focused on security & recognized among the world’s most innovative cybersecurity players
Unbiased,Vender-Agnostic Approach
Partnerships with best of breed providers, with a pulse for emerging technology trends to design & protect across any security stack
Speed & Agility Across Multi-Technology, Complex Environments
Cyber experts support the world’s largest banks, gaming companies and utility providers, offering customized and flexible solutions
Comprehensive, Holistic Security Expertise
Advisory, Implementation, Identity, Managed Security Services, Digital Forensics and Incident Response Services
