Threat Advisory: OAuth Phishing Awareness
July 24, 2019

Traditional phishing messages often target users to deliver malware or obtain credentials. New tools are being released that also enable OAuth abuse in phishing attacks. OAuth has become the de-facto protocol used by companies such as Google, Facebook, Amazon, and Microsoft to manage access to user data across their platforms.
However, this creates an opportunity for an attacker to leverage a malicious application and, upon tricking a user into granting access, make requests, enabling them to perform actions such as:
- Searching for and reading specific messages
- Installing filtering and forwarding rules
- Downloading messages, attachments, and files (including from OneDrive/SharePoint, etc.)
- Injecting macros into stored Word documents
These techniques have been observed in sophisticated attacks in the past1 but are becoming easier to execute and are gaining in popularity. Specific policies, technology, and monitoring needs to be in place to detect these types of attacks.
Please see the Recommendations section below for more information.
Details
OAuth allows an “application” to request access to a “resource” and for permissions to be granted by a “resource owner”. These requests are processed by an “Authorization Server” which presents the Resource Owner with an interface to allow or deny the request. Once granted, the account access will persist until explicitly revoked; even through password resets or 2-factor authentication changes.
A malicious actor could craft an Application using a well-known platform like Google or O365 and send a request, via a phishing attack, to obtain an access token from the Resource. An example phishing message may look like the following4:
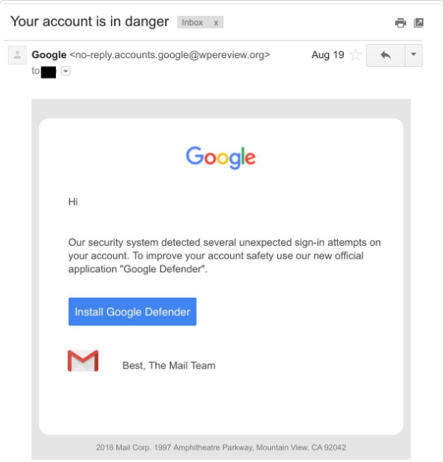
Based on the specific scope requested by the attacker, it may be possible for them to perform any of the following actions:
- Reading mail messages
- Searching the user's mailbox
- Reading the user's contacts
- Downloading messages and attachments
- Searching OneDrive and downloading files
- Sending messages on behalf of the user
- Extraction of e-mails matching specific keywords
- Creation of malicious Outlook Rules
- Extraction of files from OneDrive/Sharepoint
- Macro injection on stored word documents
The full extent of the attacker’s capabilities depends on the specific resource they’re requesting data from.
Recommendations
Several toolkits2,3 have been designed to enable Red Teams to test an organization’s defenses. As the barrier to entry is lowered, and more tools are released publicly, OAuth attacks may become more common and lead to an increase in incidents involving malicious 3rd party applications. Organizations need to be able to detect and respond6 to these potential incidents. Mitigation and detection of OAuth attacks may include:
Phishing Testing and Defense:
- Training for how to spot phishing messages and specifically OAuth phishing
- Simple method to allow employees to submit and validate suspicious email messages
- Test defense and response to these types of attacks
OAuth Specific Recommendations:
- Limit the scope 3rd party apps can request
- Disable 3rd party apps across the organization where possible
- Query and monitor for all consented applications (Identify rare or suspicious instances)
- 0365: Monitor “app permissions” in Cloud App Security5
If a suspicious or malicious 3rd party application is identified in the environment the permissions should be revoked and access logs should be reviewed to understand the scope of the compromise.
Herjavec Group's Threat Management & Incident Response team is available for further support and consultation. Please contact us here.
References
- https://blog.trendmicro.com/trendlabs-security-intelligence/pawn-storm-abuses-open-authentication-advanced-social-engineering-attacks/
- https://github.com/fireeye/PwnAuth
- https://github.com/mdsecactivebreach/o365-attack-toolkit
- https://blog.trendmicro.com/trendlabs-security-intelligence/pawn-storm-abuses-open-authentication-advanced-social-engineering-attacks/
- https://docs.microsoft.com/en-us/cloud-app-security/manage-app-permissions
- https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-types
For Managed Services customers, our Managed Services team will engage with the appropriate technical contacts in your respective organizations directly to provide alerts, escalations, actions and or reports based our service agreement with you. If you have questions or concerns, please engage your Herjavec Group account representative directly or contact Herjavec Group.
