Herjavec Group LockBit 2.0 Ransomware Profile
August 23, 2021

LockBit ransomware was initially discovered in September 2019. Since then, the malware has been used in ransomware attacks against a range of industries located across the globe. With the evolution of ransomware operators and their tactics over the past few years, groups like the LockBit gang have implemented successful tactics from other groups to increase their success and/or profits. In the LockBit group's newest campaigns, they have rebranded themselves as "LockBit 2. 0", a double-extortive Ransomware-As-A-Service (RaaS) operation.
Since at least June 2021, the LockBit group started advertising "LockBit 2.0" as their new and improved version of the ransomware. Along with this new version came a slightly updated payment site and information stealing functionality for "double-extortion" purposes. This is the act of exfiltrating sensitive data from the victim network before the encryption stage of the attack[1]. Malware analysis researchers have also discovered that LockBit 2.0 weaponizes Active Directory Group Policy Objects (GPOs) to further assist with accomplishing its goals, and consider this a novel demonstration of attack procedures [2]. LockBit 2.0 introduces even more social-engineering aspects to their operations by changing the wallpaper of encrypted systems to display a message that says: "offering the opportunity to earn millions of dollars to anyone [that provides a method] into a corporate network environment" - such as with RDP or VPN login credentials after a successful ransom[3]. LockBit 2.0 also weaponizes legitimate LOLBAS (Living off the Land Binaries and Scripts) such as sysadmin tools Process Hacker and PC Hunter, to terminate processes and services in the victim system [4]
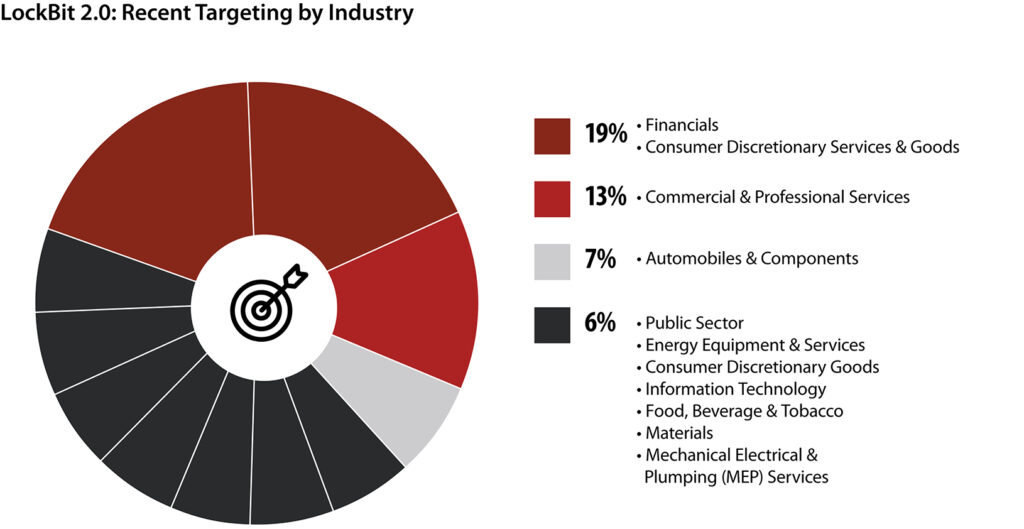
Targeting
Some of LockBit 2.0's most recent confirmed targets have included:
|
Name |
Description |
Industry |
Country |
|
Accenture |
An international professional services firm with HQ in Ireland. |
Commercial & Professional Services |
Ireland |
|
Deckx Garage |
A Ford dealership in Belgium. |
Consumer Discretionary Services & Goods |
Belgium |
|
J Jaramillo Insurance |
An insurance company in Puerto Rico. |
Financials |
America |
|
JINYANG |
A manufacturer of rubber parts in Korea. |
Automobiles & Components |
Korea |
|
Le Monastery |
A Canadian resident and apartment provider for seniors |
Financials |
Canada |
|
LivingFlame |
A luxury gas fireplace manufacturer in New Zealand |
Consumer Discretionary Services & Goods |
New Zealand |
|
Marlabs |
A digital technology solutions company in the US |
Information Technology |
America |
|
Mecc Alte |
A manufacturer of mechanical-electrical alternators in Italy |
Energy Equipment & Services |
Italy |
|
MK Brokers |
A Bulgarian licensed investment intermediary |
Financials |
Bulgaria |
|
Pike County |
A police department in Petersburg, Indiana |
Public Sector |
America |
|
Pulmuone Food USA |
A US food producer |
Food, Beverage & Tobacco |
America |
|
Salee Printing |
A packaging solutions provider in Thailand |
Commercial & Professional Services |
Thailand |
|
Seliner Schreinerei AG |
A furniture manufacturer and design company in Switzerland |
Consumer Discretionary Services & Goods |
Switzerland |
|
Inline Plumbing & Electrical |
A plumbing company in Australia |
Mechanical Electrical and Plumbing (MEP) Services |
Australia |
|
Phoenix Services |
A property maintenance company in New Zealand |
Consumer Discretionary Services & Goods |
New Zealand |
|
Haydn |
A painting supplies company in New Zealand |
Materials |
New Zealand |
LockBit 2.0 ATT&CK Lifecycle
The LockBit group operators have been observed carrying out ransomware attacks with the following steps:
-
- Gain initial access to target environments by exploiting public-facing applications and employing the services of "Initial Access Brokers" (IABs). IABs are financially motivated individuals or groups who provide ransomware operators with access to a silently compromised network in exchange for receiving a small fee or direct employment from ransomware operators [5] (T1078 Valid Accounts, T113 External Remote Services). As of August 6, 2021, the Australian Cyber Security Centre has confirmed that LockBit 2.0 operators have successfully gained initial access during attack campaigns via exploitation of vulnerabilities (Exploit public-facing application) in Fortinet software components, such as the long-existing vulnerability FortiOS software components tracked under CVE-2018-13379 [6].
- Load Component Object Model (COM) Objects and win32 DLL modules which are leveraged to achieve persistence and mounting the encryption stage of the attack (T1106 Native API, T1559.001 Inter-process Communication: Component Object Model).
- Check the Windows Registry for system information and the system s supported languages (T1082 System Information Discovery).
- Enumerate AppData\Local\Microsoft\Windows\Temporary Internet Files and \AppData\Roaming\Windows\Cookies (T1083 File and Directory Discovery).
- Add itself to the HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion registry for persistence (T1547.001 Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder).
- Write a key named "Public" to HKEY_CURRENT_USER\Software\LockBit in hexadecimal (T1112 Modify Registry).
During analysis of a LockBit binary by Herjavec Group Threat & Vulnerability Management Team; at least one sample wrote the following value to the registry [7]:
Name: Public
Operation: write
typeValue: REG_BINARY
value: B30CCB29A6DF27345A4CF518B1DA87346628747DF2FD16A6C3A9CB5F3FB38358C4A95DD
94C8D3CF4F72A30EDA5984B3621F64942CD377C67719FC409076D7F0170D4472054D15479BB9EB
44B88DD2306EF51C00C5E1F9127C155144D80D56CDF6606F02A40F515230F7DE88AC12628CE88
16C8BAA3B0398A134DF4562F31FFD2D7BFA4C5202E3A901FB0F96AA8C3198542593CB67E0AAB1
B65D1D92713F65C84C753095D9C505650D9D4B43A726D48AD0BDFC905269DBFAC30907BB77837
BBF30BBD0C24A13C8F0F3DB85240AAF51C0EE56B69A7DA2C2F8E339A86935E4D78AF9B4672BC
0873B2746656C91BAB8E6A45EE0AE1A3D546CB44D308C11A133ACFC301000
- Use Group Policy Objects (GPO) to disable and impede native Windows security functionalities (T1484.001 Domain Policy Modification: Group Policy Modification, T1562 Impair Defenses: Disable Windows Event Logging,T162.001 Impair Defenses: Disable or Modify Tools).
[General] Version=%s displayName=%s
[Software\Policies\Microsoft\Windows Defender;DisableAntiSpyware]
[Software\Policies\Microsoft\Windows Defender\Real-Time Protection;DisableRealtimeMonitoring]
[Software\Policies\Microsoft\Windows Defender\Spynet;SubmitSamplesConsent]
[Software\Policies\Microsoft\Windows Defender\Threats;Threats_ThreatSeverityDefaultAction]
[Software\Policies\Microsoft\Windows Defender\Threats\ThreatSeverityDefaultAction]
[Software\Policies\Microsoft\Windows Defender\Threats\ThreatSeverityDefaultAction]
[Software\Policies\Microsoft\Windows Defender\Threats\ThreatSeverityDefaultAction]
[Software\Policies\Microsoft\Windows Defender\Threats\ThreatSeverityDefaultAction]
[Software\Policies\Microsoft\Windows Defender\UX Configuration;Notification_Suppress]
- Use cmd,exe (T1059.003 Command and Scripting Interpreter: Windows Command Shell) to:
- Use wmic (T1047Windows Management Instrumentation) as an orchestrator by instructing(T1490Inhibit System Recovery)
- vssadmin to delete shadow copies
- bcdedit to disable recovery
- lafand wbadmin to delete any backups
- Use wmic (T1047Windows Management Instrumentation) as an orchestrator by instructing(T1490Inhibit System Recovery)
-
- Delete the Windows System, Application, and Security logs from the Windows Eventlog (T1070.001 Indicator Removal on Host: Clear Windows Event Logs):
-
Inject the adversary-crafted code into the svchost.exe process (T1055.002: Process Injection: Portable Executable Injection), and the beginning of the encryption process.
-
Begin the encryption process and drop the ransom note in each folder after it encrypts the folder's contents (T1486: Data Encrypted for Impact).
Defensive Recommendations for Observed Tactics, Techniques, and Procedures
Herjavec Group recommends the following strategies to prevent or mitigate the risk of LockBit 2.0:
- Keep externally facing devices up to date with security patches.
- Enable multifactor authentication (MFA) for all user accounts if possible.
- Educate users on strong passwords and the dangers of re-using old passwords.
- Consider network segmentation and monitoring or restricting traffic protocols associated with lateral movement, such as SMB if able.
- Employ the principle of least privilege to operating systems and applications based on user roles and duties.
- Develop or employ the use of third-party relationship and dark-web monitoring services to proactively handle credential leaks associated with valid third-party accounts.
- Perform frequent backups and recovery tasks based on system criticality (daily, weekly, or monthly), and keep backups offline and encrypted.
References
- "2021-006: ACSC Ransomware Profile - Lockbit 0 I Cyber.gov.au:' https://www.cyber.gov.au/acsc/view-all-content/advisories/2021-006-acsc-ransomware-profile-lockbit-20 (accessed Aug. 18, 2021).
- "LockBit 2.0, the first ransomware that uses group policies to encrypt Windows domains;' Security Affairs, 29, 2021. Accessed: Aug. 18, 2021. [Online]. Available: https://securityaffa irs.co/word press/120664/ cyber-cri me/lockbit-2-0-ransomware-group-policies.htmI
- Abrams, "LockBit ransomware recruiting insiders to breach corporate networks;' BleepingComputer, Aug. 04, 2021. Accessed: Aug. 18, 2021. [Online]. Available: https://www.bleepingcomputer.com/news/security/lockbit-ransomware-recruiting-insiders-to-breach-corporate-networks/
- P. Bernardo, J. Chong, N. Madayag, M. Marti, C.Tomboc, and S. Torre,"LockBit Resurfaces With Version 2.0 Ransomware Detections in Chile, Italy, Taiwan, UK;'Trend Micro, Aug. 2021. Accessed: Aug. 18, 2021. [Online]. Available: https://www.trendmicro.com/en_us/research/21/h/lockbit-resurfaces-with-version-2-0-ransomware-detections-in-chi.html
- Kivilevich, "All Access Pass: Five Trends with Initial Access Brokers;' Kela, Aug. 2021. Accessed: Aug. 18, 2021. [Online]. Available: https://ke-la.com/all-access-pass-five-trends-with-initialaccess-brokers/
- Federal Bureau of Investigation, Cyber Division, "APT Actors Exploiting Fortinet Vulnerabilities to Gain Access for Malicious Activity;' FBI, Ml-000148-MW, May 2021. Accessed: May 28, 2021. [Online]. Available: https://www.ic3.gov/Media/News/2021/210527.pdf
- Lockbit MD5:69bec32d50744293e85606a5e8f80425. RUN, 2021. Accessed: Aug. 18, 2021. [Online]. Available: https://app.any.run/tasks/d4614d8c-cbcc-43cc-99f7-12737f680e00/