Threat Advisory: Russian State-Sponsored Malicious Cyber Actors Exploiting CVE-2020-4006
December 8, 2020

The NSA recently released an advisory on Russian state-sponsored malicious actors exploiting CVE-2020-4006, a command-injection vulnerability in several VMWare Access and VMWare Identity Management Products. VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector have been identified containing a command injection vulnerability. If successful, the exploit allows a potential malicious actor, with network access to the administrative configurator (contained on port 8443) and a valid set of administrative accounts, to execute commands with unrestricted privileges on the underlying operating system.
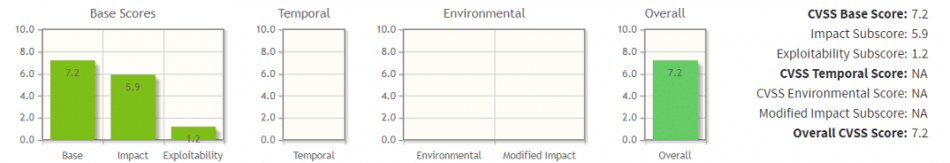
CVSS 3.1 score of HIGH - 7.2 by NVD Analysts of the NIST National Vulnerability Database
The vulnerability affects the following VMware product’s:
- VMware Workspace ONE Access 20.10 (Linux)
- VMware Workspace ONE Access 20.01 (Linux)
- VMware Identity Manager 3.3.3 (Linux)
- VMware Identity Manager 3.3.2 (Linux)
- VMware Identity Manager 3.3.1 (Linux)
- VMware Identity Manager Connector 3.3.2, 3.3.1 (Linux)
- VMware Identity Manager Connector 3.3.3, 3.3.2, 3.3.1 (Windows)
- VMware Identity Manager Connector 19.03.0.0, 19.03.0.1
Russian state-sponsored threat actors have been identified exploiting this vulnerability via command injection (T1059 Command and Scripting Interpreter) leading to the installation of a web shell (T1505.003 Server Software Component: Web Shell). From this web shell, SAML authentication assertions are then generated and authorized by Microsoft Active Directory Federation Services (ADFS) (T1212 Exploitation for Credential Access), granting access to unrestricted access to the data on the underlying system’s data (Tactic TA0009 Collection).
In their disclosure, VMware provided a temporary workaround that could be implemented until an official fix was released that resolves the vulnerability in the affected software applications.
However, Herjavec Group strongly recommends patching the affected systems as soon as possible, following the newest guidance provided by VMWare within their Knowledge-Base Document 81754 (KB18754). Any temporary solution provided is only meant to function as a work-around for patching until they can be updated at the most appropriate time.
If the following advisory is applicable to your environment, Herjavec Group recommends your IT team review the technical details included and monitor your environment for any susceptible systems. Herjavec Group’s analysts are working with applicable vendor partners to apply detection and mitigation strategies where appropriate. For Managed Services customers, our Managed Services team will engage with the appropriate technical contacts in your respective organizations directly to provide alerts, escalations, actions, and or reports based on our service agreement with you. If you have questions or concerns, please engage your Herjavec Group account representative directly or contact Herjavec Group.
For more information on Threat Advisories, our Managed Security Services and SOC Operations, Security Engineering, or Incident Response, please connect with a security specialist.
References
- VMWare, “VMSA-2020-0027-2,” VMware, Nov. 23, 2020. https://www.vmware.com/security/advisories/VMSA-2020-0027.html (accessed Dec. 07, 2020).
- National Security Agency, “Russian State-Sponsored Actors Exploiting Vulnerability in VMware® Workspace ONE Access Using Compromised Credentials,” Cyberscurity Advisory | U/OO/195076-20 | PP-20-1385, Dec. 2020. Accessed: Dec. 07, 2020. [Online]. Available: https://media.defense.gov/2020/Dec/07/2002547071/-1/-1/0/CSA_VMWARE%20ACCESS_U_OO_195076_20.PDF.
- NIST NVD, “CVE-2020-4006 Detail | National Vulnerability Database,” Dec. 03, 2020. https://nvd.nist.gov/vuln/detail/CVE-2020-4006 (accessed Dec. 07, 2020).
- “VMware Workspace ONE Access, VMware Identity Manager, VMware Identity Manager Connector Workaround Instructions for CVE-2020-4006 (81731).” https://kb.vmware.com/s/article/81731 (accessed Dec. 07, 2020).
- S. Gatlan, “VMware discloses critical zero-day vulnerability in Workspace One,” BleepingComputer, November 23, 23020. https://www.bleepingcomputer.com/news/security/vmware-discloses-critical-zero-day-vulnerability-in-workspace-one/ (accessed Dec. 07, 2020).
- “CSA_VMWARE ACCESS_U_OO_195076_20.pdf.” Accessed: Dec. 07, 2020. [Online]. Available: https://media.defense.gov/2020/Dec/07/2002547071/-1/-1/0/CSA_VMWARE%20ACCESS_U_OO_195076_20.PDF.